Alert News📣
The latest phishing campaign is making waves in the market. WordPress users receive a phishing email from the WordPress team highlighting a Remote Code Execution susceptibility on their websites.
The email uses an identifier CVE-2023-45124, but unfortunately, this is not a legitimate CVE (Common Vulnerabilities and Exposures). As a result, users may download and install a “Patch” plugin.
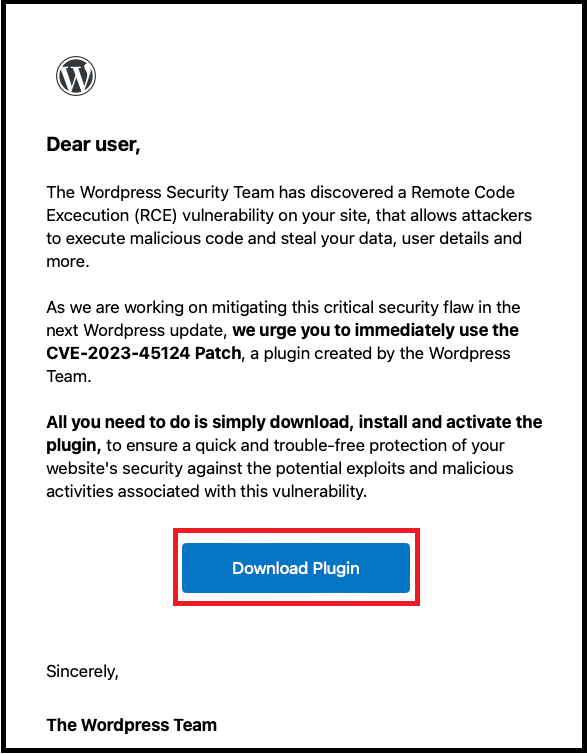
When users click the malicious “Download Plugin” link, they are redirected to a fake landing page at en-gb-wordpress[.] org:
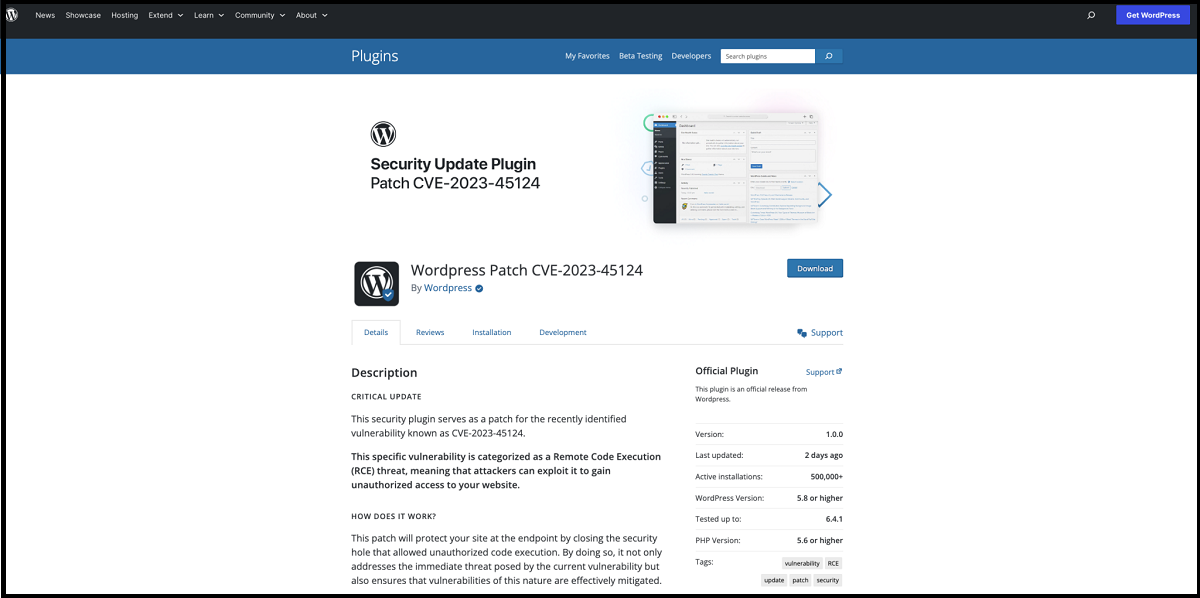
Furthermore, the installed plugin uses a wpress-security-wordpress slug and incorporates a harmful administrator user. The administrator user has a username wpsecuritypatch.
The plugin then sends the site URL and generates a password for the user to return to a Command and Control (C2) domain, i.e., wpgate[.] zip. Surprisingly, the plugin has a functionality that helps the user remain invisible.
In addition, the plugin saves the separate backdoor by the name of a filename wp-autoload.php in the webroot after downloading it from the C2 domain wpgate[.] zip.
The backdoor has a password consisting of a SQL Client, a Command Line terminal, a file manager, and server environment information.
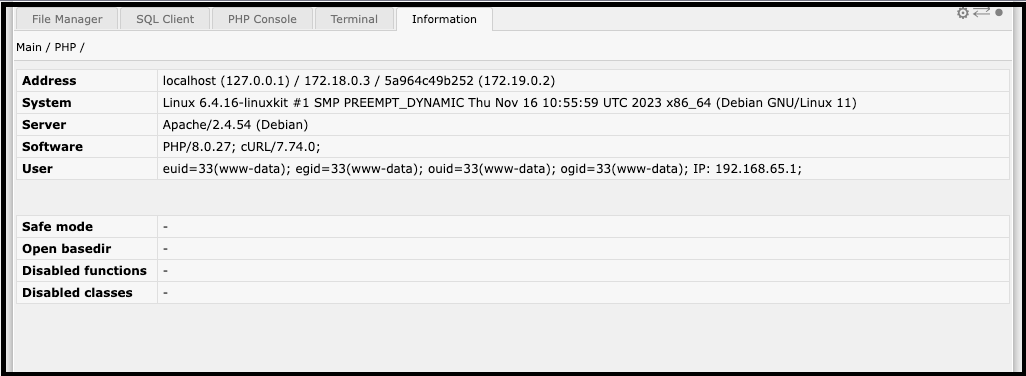
This way, attackers can anonymously control users’ websites for longer and modify them to accomplish their notorious objectives.
Signs Of A Website Compromise
Whether your website has been compromised due to CVE-2023-45124 phishing scam or not, you can check the following indicators:
- An invisible admin user has a username wpsecuritypatch
- A plugin has a slug wpress-security-wordpress
- A wp-autoload.php file in the webroot
- Malicious domains like en-gb-wordpress[.] org, and wpgate[.] zip
Official Response from WordPress
In response to fake phishing scams containing malware, WordPress has officially stated:
“The WordPress Security Team will never email you requesting that you install a plugin or theme on your site and will never ask for an administrator username and password.”
You will receive official emails from WordPress with domains such as @wordpress.org or @wordpress.net. Similarly, these emails will include digital signatures associated with the official WordPress organization.
In case you receive an email stating you should install a plugin on your website using the specific username and password, delete such emails from your inbox immediately.
Moreover, you must report them to your email service provider urgently.
Unfortunately, these emails have been associated with a malicious website resembling a WordPress plugin repository. However, this is not the case in reality.
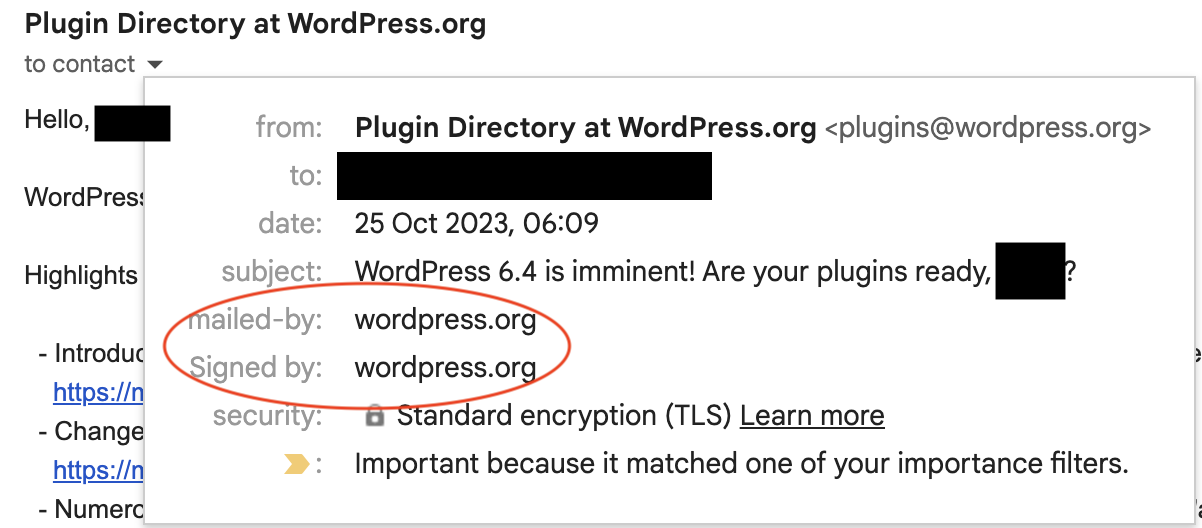
Besides, the WordPress security team interacts with WordPress users via the following locations:
- wordpress.org/security (For visiting the Making WordPress Secure blog)
- org/news (for getting the latest news and happenings related to WordPress)
Likewise, the WordPress plugin team does not interact with WordPress users directly. They can email plugin support staff, contributors, and owners through [email protected].
If WordPress users want to access the official WordPress plugin repository, they should visit wordpress.org/plugins. The repository has internationalized versions on various subdomains like fr.wordpress.org/plugins, en-au.wordpress.org/plugins, etc.
Share the News, and Stay Safe!